Many phishing emails attempt to deceive the recipient by posing as a new voicemail message. Many of you have referred these to me for verification. Thank you!
With that in mind, I wanted to explain how to recognize valid voicemail notifications sent from our voicemail server via email. Below is an example of a real voicemail notification from our system. Pay attention to the six following characteristics of this email.
- The “pretty” From address, underlined in red, is “IP Office Voicemail Pro Server.
- The actual sending email address, underlined in blue is <no-reply-voicemail@berry.edu>.
- The subject, which is directly below the red and blue lines, contains only “Voicemail Message”, the number that called (or possibly a name IF the system can resolve it via CallerID, but in that case, the call most likely came from on-campus) with an “arrow” pointing to your phone number or email username. It then repeats the “From” information. Notably, it DOES NOT contain a person’s name, i.e. “Olivia left you a message”.
- The attachment, circled in red, is a .WAV file, a type of audio file.
- The only text in the body of the email, circled in blue, is “IP Office Voicemail redirected message”.
- The area above this text, partially highlighted in yellow, DOES NOT contain the external email banner.
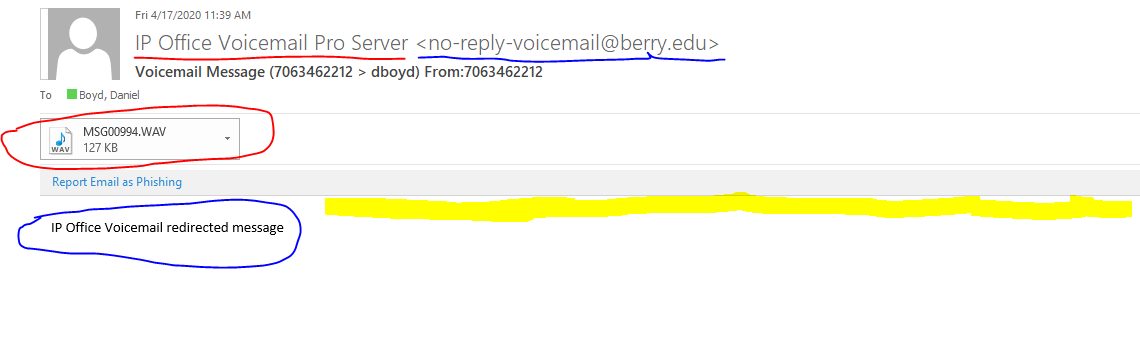
This is what a valid voicemail notification looks like. There is no indication of the length of the message, other than the size of the audio file, which will vary based on length and content.
Bonus information: The message attached to this email is about twenty seconds long. You’ll notice the file size is 127KB. Files smaller than 30KB most likely do not have any content at all.
I hope this helps you determine the validity of voicemail notification. As always, if you still have questions, please contact Information Security by emailing infosec@berry.edu or by calling extension 1750, or 706-236-1750.
Return to the Quick Info main page
Return to the InfoSec News and Alerts front page
Photo Credit: Photo by Quino Al on Unsplash

