The days keep marching on! It’s November already and holidays and finals are growing ever closer. Fall weather is finally here, just in time for winter to blow in.
I want to thank everyone who came by the table in Krannert during National Cyber Security Awareness Month in October. We had more people stop by this year than ever before and one lucky person won the big prize on Halloween. In addition to some Berry-branded drinking apparatus, they got lots of candy and a Yubico YubiKey that will help them increase the security on lots of their online accounts. There were over 60 visits to the table this year, the weekly articles were viewed over 170 times and the videos had dozens of views. I hope you had as much fun watching the last two videos as I did writing and making them.
Another piece of information I want to pass along is the implementation of automatic idle lock for campus workstations. This has been mentioned before, but to refresh your memory, this simply means that most computers on campus, if left idle for ten minutes, will lock the desktop, requiring the user to enter their credentials to gain access. Information Technology has been working hard to make sure this policy does not impact computers in classrooms, meeting rooms, and other places where there is a potential for the policy to interrupt class or meetings. The important information I want to pass along is that this policy will go into effect on January 6th, 2020, when everyone returns from the holidays. More information will be provided between now and the end of the semester.
Keep an eye on this site to see when the next Krannert table is scheduled. The front page has an “Events” link in the main menu that will show all of the upcoming events being offered by Information Security. Also listed on the events page will be any upcoming LunchITS, where we dig into a topic for the duration of the lunch hour while enjoying our lunch. There will be one in early November, but the date is not yet finalized.
You can also check back for warnings about current phishing emails, confirmations of valid emails you might have a question about, and data breach notifications. There’s also the Q&A section, where you can ask a question and get an answer directly from me.
If you notice any issues with the site, as it is undergoing an upgrade and expansion, please let me know by emailing infosec@berry.edu.
Let’s take a few moments and dig into this month’s topic. Data security.
As I hope you inferred from all of the events and activity during October, information security efforts will only be successful when all members of the campus community understand the risks and take steps to avoid them. One of the biggest risks is the exposure of confidential data.
Did you know? In 2017 the education industry (which includes K–12 and higher education institutions) had 7,837,781 records breached in 35 events. To put that into perspective, the healthcare industry had 6,058,989 records breached in 428 events, and the retail industry had 123,652,526 records beached across 33 events. (See Privacy Rights Clearinghouse Chronology of Data Breaches, 2017 data.)
More than half of the breaches in the education sector were caused by activities directly attributable to human error, including lost devices, physical loss, and unintended disclosure (see figure 1). These breaches were arguably preventable through basic information security protection safeguards.
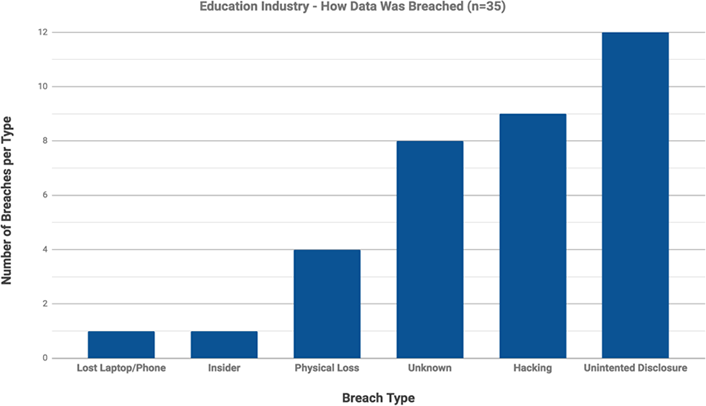
What can you do every day to protect data? There are very few, if any, verticals such as higher education that transmit, process, access, and share such varying sensitive data elements. There is not a “one size fits all” blueprint for information security controls that all institutions can follow. Yet all campus members have a responsibility to know basic information security protections to safeguard data and prevent those data from being mishandled:
- Update your computing devices: Ensure updates to your operating system, web browser, and applications are being performed on all personal and institution-issued devices. Updates to college owned computers is handled automatically as long as it is online to receive the update and is rebooted on a regular basis.
- Use multi-factor authentication: Whether for personal use or work, multi-factor authentication (MFA) can prevent unauthorized access even if your login credentials are stolen or lost. If you would like MFA enabled for your account, please email computing@berry.edu and request it.
- Create really strong and unique passwords: Create unique passwords for all personal and work accounts. In today’s environment, one of the best ways to create a really strong password is to use a password manager for all of your accounts. A password manager will alleviate the burden of having to memorize all the different complex passwords you’ve created by managing them all in one “vault” and locking that vault with a single master password.
- Protect your devices: Using biometrics or six-digit passcodes on smartphones and tablets is critical to keeping curious minds from accessing personal information, work email, or retail/banking applications. It also helps protect your device if you lose or misplace it.
- Understand where, how, and to whom you are sending data: Many breaches occur because of “oopsie moments” where we accidentally post sensitive information publicly, mishandle or send to the wrong party via publishing online, or send sensitive information in an email to the wrong person. Taking care to know how you are transmitting or posting data is critical.
Getting ready to send data to a vendor or sign a contract? With more and more services moving to the cloud, higher education institutions have an additional obligation to ensure that third parties are protecting our most sensitive information. If you or your department is looking to purchase or adopt a service or technology that uses institutional data, it is imperative that you include the Office of Information Technology (OIT) at the beginning of the project or contract process to help ensure that data are properly protected. To determine whether or not OIT should be involved in the vendor/contract process, ask yourself the following questions:
- Does the project (and in-scope technologies) involve the handling or storage of personal data (e.g., student data, employee data, donor data, research data, or financial data)?
- Does the project (and in-scope technologies) involve the handling or storage of personal data that is regulated by government entities or has special contractual obligations to a third party (e.g., contract sponsored for research)?
- Is there transfer of any institutional data from an institution-owned system or device to a third-party vendor-contracted system or device?
- Does the project involve acquiring/implementing/developing software, services, or components that your institution has not previously deployed?
- Does the project involve providing a new data feed to an existing campus partner?
- Does the project involve accepting card payments in any way?
If the answer to any of the above questions is “yes,” please collaborate with OIT at the beginning of the project to ensure that institutional data are properly protected. You can simply email computing@berry.edu and let the Technical Support Desk know you have a new service you want to implement. They will get the right staff in touch with you.
Have a great November!
Photo by Priscilla Du Preez on Unsplash

 November News from Information Security
November News from Information Security



 October News from Information Security
October News from Information Security
