Welcome to the very late June newsletter!
A failure to plan and pre-write the June newsletter, plus a virtual conference during the first week of June, then a frenzy of activity at work, then a couple of vacation days has pushed this edition way past its normal publishing date.
But here we are, still stewing in the social distancing mire, but at least able to do more things, like eat AT restaurants instead of getting food delivered, or, gasp!, going out and picking it up curbside. I hope all of you are healthy and well and have been able to resume some sense of “old normalcy”.
As I mentioned in the last newsletter, phishers, scammers, and the like have been VERY busy trying to take advantage of this time of flux, if not outright chaos. I write this newsletter as cities around the country stagger under the effects of not just the coronavirus, but protests and riots. Both are happening, and many protests that start peacefully are stirred into riots by organized bad actors. I hope you or your loved ones have not been affected…and that’s all I’m going to say about that.
I’ve interacted with several of you about suspect emails over the last few weeks and I appreciate your caution and skepticism. Everything from fake voice mail notifications to fraudulent signature requests have arrived in our email inboxes. Companies continue to improperly care for the data they acquire from us. There are a couple of upcoming breach notifications that I need to finish and publish to the site.
With that said, I encourage everyone to go to Have I Been Pwned to see what data about you has been exposed. Notice I don’t say “IF” data has been exposed, but “what” data has been exposed. It’s easy. Go to the site, put in your email address(es), and be sure you are sitting down when you click “pwned?”. While you are there, sign up to be notified when information connected to your email addresses has been exposed. You’ll have to register each email individually.
As I mentioned in May’s newsletter, all email should be carefully examined. Actually, I said that “almost all emails should be considered suspect” and I stand by that statement. I also said that this was the number one safety tip I could offer during this time. Here are tips two and three.
Most Important Tip #2: Update your devices.
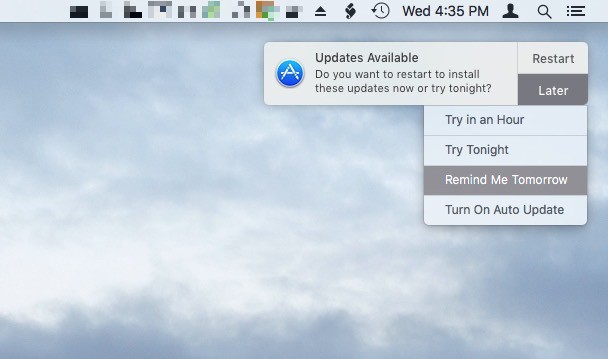
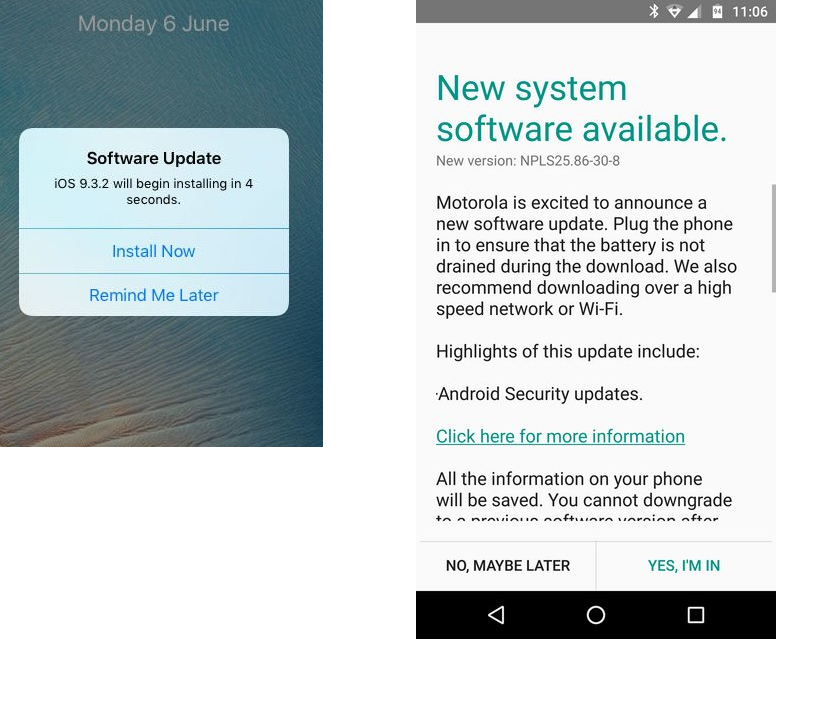
Your device, whether it is a Windows or macOS computer, or an Android or iOS device should be set to automatically update. If you have an undeniable fear of automatic updates, then at least make sure that update notifications are turned on. Then, when Windows or macOS notify you of an update, or your Android or iOS device chime to tell you an update is available, first confirm that it is a real update notification. Update notifications don’t come in your email, nor do they pop up inside your browser. These notifications come directly from the operating system of the device. Examples are shown below:
Windows 10 : 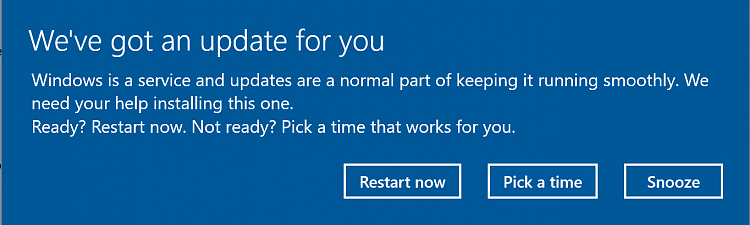
macOS:
Left iOS (iPhone and iPad) and Right Android phone (Motorola, others may vary)
Most Important Tip #3: Use a strong, unique password and multi-factor authentication for every login account you have.
What do I mean by a strong password?
- At least 13 characters long, 20 is better…
- Don’t worry about complexity unless the particular site or service requires it.
- No dictionary words by themselves.
- Do not use any part of your username or real name/nickname in the password.
What?! Thirteen characters? Twenty characters? Yes. Find a password manager you like and use it to both generate and store your passwords. That means you only need to remember one long password, to open the password manager. Longer passwords are better than short, complex passwords. If you insist on making long passwords that are non-random, don’t use long dictionary words. Use multiple, unrelated words, as explained in the Good Password Guidelines Quick Info article here on this site.
Get multi-factor authentication enabled on every account you can, especially accounts for banks and other financial sites, sites which handle your medical records, other confidential and sensitive sites, and your Berry account.
Photo Credit: Photo by Max Kleinen on Unsplash

 June News from Information Security
June News from Information Security




