March! Yay! March! The third month of the year has begun, and it will be busy, as we have reached the midpoint of the semester, and can now look forward to spring break, warmer weather, and the end of the semester. This is not to say that we don’t have plenty of challenges ahead of us. As we stare into the distance at another possible light at the end of the dark COVID tunnel, we will have to acknowledge that COVID will be endemic, but that the damaging reactions to it are hopefully, finally over. But this is a information security newsletter, so let me move on now to the information security.
No one has been able to escape the news about the Russian invasion of Ukraine, but the reason I bring it up now is warn everyone that one of the many side effects of this conflict will be increased cyber-related attacks. These attacks have and will target pretty much everything and everybody. Please be vigilant and alert to be able to spot phishing emails and other types of social engineering. I’ve found a new, simplified set of questions you should ask yourself when you receive an unexpected email, especially one that purports to be from a coworker or colleague.
- Did the email arrive unexpectedly? We’ve discussed this in the past, but it is almost always the first question to ask yourself.
- Is it the first time the sender has asked you to perform the requested action? Phishing emails almost always have an “ask” of some kind.
- Does the request include a “you need to do this NOW” statement? Urgency is another aspect of a phishing email we have discussed before.
- If the request is malicious, or is a fraudulent request, could fulfilling the “ask” harm the college by exposing it to lawsuits, blackmail, or other dire consequences?
If the answer to all or any of these questions is “Yes”, then you should regard the email as suspicious and confirm the request through an alternate means (phone call, face to face, etc.).
In addition to being vigilant about phishing emails, we should all also make sure that all of our devices, from our work computers to our phones to our personal computers, are all up to date with the latest updates. You can do this for your college-provided computer simply by regularly rebooting it. If your phone tells you an update is available, go ahead and update as soon as you can. Even your home computer should regularly check for updates unless you have disabled this feature and let you know when it needs to update. Keep your devices up to date!
I’ve written in the past about how important it is to report phishing emails. Doing so helps us protect the community as a whole. Unfortunately, some users have found the Microsoft phish reporting menu instead of the Report Email as Phishing button that Information Technology provides to send phishing and spam emails to us for investigation. That is understandable…the Microsoft reporting menu is right there on the menu bar in the web interface at mail.berry.edu. The Report Email as Phishing button is hidden in the three dots menu when you are viewing an email. It’s not the top three dots menu, but the one on the message itself. The correct three dots menu is on the right, with the big clunky arrow pointing at it. In this menu you will find the Report Email as Phishing button. See the image below for clarification.
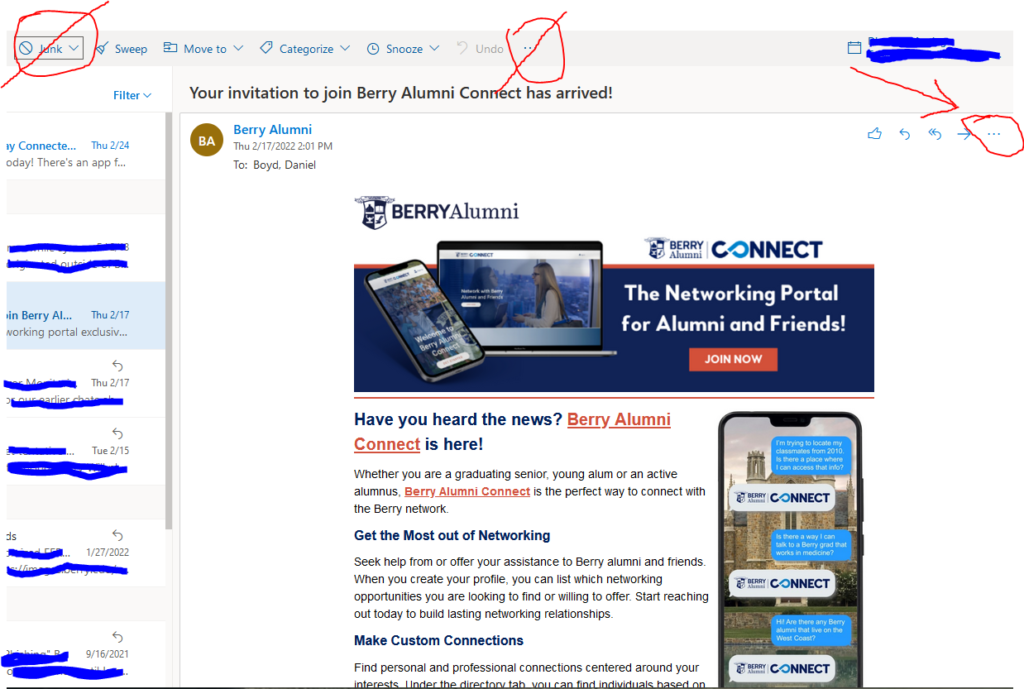
The Report Email as Phishing button looks like this in Outlook or the Outlook phone app:

Please use this to report phishing emails, as your report could save someone else from being fooled by the fraudulent email.
Finally, I want to remind everyone that you will receive an email immediately after Spring Break inviting you to complete the Cybersecurity Awareness training. We ask you do this as soon as possible and as a reminder, this should only take about 20 minutes to complete AND you don’t even have to do it all at once. I want to thank you all in advance for taking the time to complete this training. You will get another email to remind you about the training, and then the actual training invitation.
With MFA enabled on your Berry account, you should use it in the most secure way via the Microsoft Authenticator app on your smart phone. But don’t stop there! Use the Microsoft Authenticator as your second factor on any site that supports Google Authenticator. Turn MFA/2FA on everywhere you can. Yes, it will take you another few seconds to log in, but your data and account will be safer.
If I’m not covering a topic of cybersecurity you are interested in or concerned about, please let me know. I want to be your first and best resource on cybersecurity information, so let me know how I can help and inform you.
If you’re not following Berry OIT on Facebook (@BerryCollegeOIT), Twitter (@berryoit), or Instagram (@berrycollegeoit), you should be, as more information from OIT and specifically Information Security, will be provided using these outlets. If you are not into social media, you can also subscribe to get updates via email. Just use the link available in the right-hand sidebar on the current posts page.
You can always check back here for warnings about current phishing emails, confirmations of valid emails you might have a question about, and data breach notifications. There’s also the events calendar where events will be posted.
Food for Thought
No pictures today, just a deep thought (and not my own, but I did contribute the parenthetical addition)…
Man, so long as he remains free, has no more constant and agonizing anxiety than to find as quickly as possible someone (or something) to worship. – Fyodor Dostoevsky
Featured Image: Photo by Zeyad Bin Kuwair on Unsplash

 March News from Information Security
March News from Information Security


