August is here and the fall semester is just around the corner. Summer, as always, has been busy for pretty much everyone. Camps, the Governor’s Honors program, preparing for the influx of new students, updates, upgrades, refreshes – you name it and it happens during the summer. Cyber-criminals don’t take the summer off either, as evidenced from the steady stream of phishing emails reported and the information the Office of Information Technology gleans from our various security and logging systems. I almost always remind you in these newsletters to treat any unexpected email, phone call or text message with caution, which is still great advice, but what about those of you, who by the nature of your job must deal with unexpected communications all the time?
Good news! This newsletter is for you! But take the featured image to heart…
I’ll also let you know about some upcoming activities by the Office of Information Security as we approach October, when we’ll celebrate another Cybersecurity Awareness Month.
First, let’s talk about those people in departments who must deal with “unexpected” communications as part of their job. Human resources, the business office, athletics, admissions, even academic departments all have to do this to some degree. Thankfully, there are tools to help mitigate this risk, from purpose made recruiting tools where information can be gathered and documents sent instead of relying on email. Applicants for jobs are supposed to submit their information into an employment portal instead of sending via email. The college is bringing tools online to help in the business office with this issue.
But what if…?
What if a document comes in attached to an email that appears to be related to your job? What can you do to safely handle this situation? Here is an attempt to walk you through the process, step by step. WARNING: This process is not for the faint of heart! I highly recommend you simply report a suspicious email using the Report Email as Phishing button. If the email turns out to be fine, you will get it back. This process will focus on email, but adapt and apply for other forms of communication. Unfortunately, this will probably not work in every situation or job, but this is a start. Sharp-eyed readers will note that this list is almost identical to how you deal with any unexpected email, with some advanced information included.
- Look for the normal phishing red flags that might apply:
- The email has poor grammar, and words are misspelled or misused.
- The email has unusual visual spacing of words, sentences, or paragraphs.
- You don’t have any kind of relationship with the company the email claims to be from.
- The email claims to be URGENT!!!
- There are links you must follow or documents you must open to resolve the urgent situation.
- If the email claims to be from someone you know, but something seems odd, contact the other person by another means (phone call, face to face, etc.). DON’T just reply to the email, this is what the attacker is hoping for…
- Make sure the sender address and the purported company match. Email from Amazon or other reputable companies will NOT come from a GMail address (unless maybe it is from Google…).
- Confirm via an alternate channel (already mentioned once, but in relation to dealing with communication that appears to be from someone you know).
- If the link is in the form of a “shortened” URL, i.e. a “bit.ly”, “tinyurl.com”, or other obviously short domains, realize this is VERY shady, and you will need to “expand” it if you still think the email is legitimate. Submit it to https://expandurl.net, then copy the result of the expanded address. Submit this using the instructions below.
- Scan the link or document using VirusTotal
- Right-click on the link and Copy it, or…
- Save the document to your system (right-click or drop-down menu and Save As…)
- Open https://virustotal.com in a web browser
- Choose the correct scanning tab-File or URL (for links)
- Paste the link or select the file using Choose File
- Click “Submit” or press Enter
- Sit back while the system scans the link or document. This will take less than a minute.
- If everything comes back clean, don’t breathe a sigh of relief yet. There still could be an issue with the file or link.
- If you still think you need to open the document or follow the link, but you are hesitant to “walk on the wild side” drop me an email or give me a call. For the brave…continue on.
- Make sure your Sophos antivirus is up to date. Make sure your operating system is up to date. Make sure your copy of Office or Adobe Acrobat (for PDF files) is up to date. If you don’t know how to do these things, please consider stopping now and contacting me.
- If you are dealing with a link, follow these steps:
- Open a new, private browsing session by going to your browser’s main menu and selecting “New private window” or “New Incognito window”.
- Paste the link into the address bar and press Enter
- Check the address again. If it is considerably different from what you pasted into the address bar, that is another strike against this being legitimate. If the page is asking you to log in to Office365 or some other site, yet doesn’t look right, close the private browser and assume the link is malicious.
- If you are dealing with a file, follow these steps:
- Double check the file extension. It might have “pdf” or “doc/docx” in the filename, but that doesn’t mean it is either of these. If the file has a “htm”, “html”, or “exe” extension, delete it and move on.
- If the extension is correct, take a deep breath. Don’t just double-click the file. Open the application required, Word or other document editor for text documents, Excel or another spreadsheet program for spreadsheets, Adobe Acrobat or some other PDF viewer for PDF files. Using the application menus, open the file. If it fails to open or if the application asks you to enable macros or there is a message about downloading additional components or plug-ins to see the file contents, assume the file is malicious. Close the application and delete the file.
- If the file opens normally, you can now see if it is indeed something you should be concerned about or must handle.
That’s a lot of “ifs” in a set of instructions, but it is what it is. Uncertainty is a certainty these days. The last step you should take when handling communications like this that turn out be be fine, is to gently chastise the sender to not send such “phishy” email.
Whew! That was intense, right? What else is happening in Information Security at Berry College? I’m glad you (or somebody) asked. With August here, that means that October and Cybersecurity Awareness Month are not far off. To “celebrate” this time, we will be exercising our minds by taking campus-wide cybersecurity awareness training. That’s right! Just like we did in the spring, we will all be offered the opportunity to learn (oooh, that’s what we do here!). While some of the information will be similar to what was in the spring training course (and repetition is a good thing), there will be new information derived from new tactics and attacks from cyber-criminals.
Also during the early part of October, we will conduct simulated phishing attacks. We were supposed to start these in the spring along with the training course, but there were some complications (<cough> COVID!) that interfered with my ability to do this. As I mentioned in my previous announcement about simulated phishing, there is NO penalty for not spotting and reporting the email, but if you do spot it, you should report it! Here is what I said in the May newsletter:
we will send out a fake phishing email (is that a double negative?) to faculty and staff, measuring to see how well we have succeeded in teaching about phishing emails over the almost four years of work we have done in cybersecurity awareness. Let me be real clear here: There is no penalty for “missing” the email by clicking on a link or opening an attachment. This is strictly to see where we are in regard to awareness.
REPEAT: There is NO penalty for falling for the fake phishing email. There will be no strongly worded emails, no walls of shame, and no follow up calls from the Director of Information Security. NOTHING!
Both of these activities will happen in the early part of October.
I’ve talked some about the Report Email as Phishing button in this newsletter. Those of you paying attention will notice that the button no longer says “Report Email as Phishing”. This is due to an update we installed recently and will be corrected this week.
That’s it! This was a heavily “technical” newsletter and I may take the contents and post them on the Cybersecurity News and Alerts site as either a Quick Info page or as a more detailed “how-to” page. I hope you find this information useful and good luck as we welcome students back in just a few days.
You all have MFA enabled on your Berry account, and you should use it in the most secure way via the Microsoft Authenticator app on your smart phone. But don’t stop there! Use the Microsoft Authenticator as your second factor on any site that supports Google Authenticator. Turn MFA/2FA on everywhere you can. Yes, it will take you another few seconds to log in, but your data and account will be safer.
If I’m not covering a topic of cybersecurity you are interested in or concerned about, please let me know. I want to be your first and best resource on cybersecurity information, so let me know how I can help and inform you.
If you’re not following Berry OIT on Facebook (@BerryCollegeOIT), Twitter (@berryoit), or Instagram (@berrycollegeoit), you should be, as more information from OIT and specifically Information Security, will be provided using these outlets. If you are not into social media, you can also subscribe to get updates via email. Just use the link available in the right-hand sidebar on the current posts page.
You can always check back here for warnings about current phishing emails, confirmations of valid emails you might have a question about, and data breach notifications. There’s also the events calendar where events will be posted.
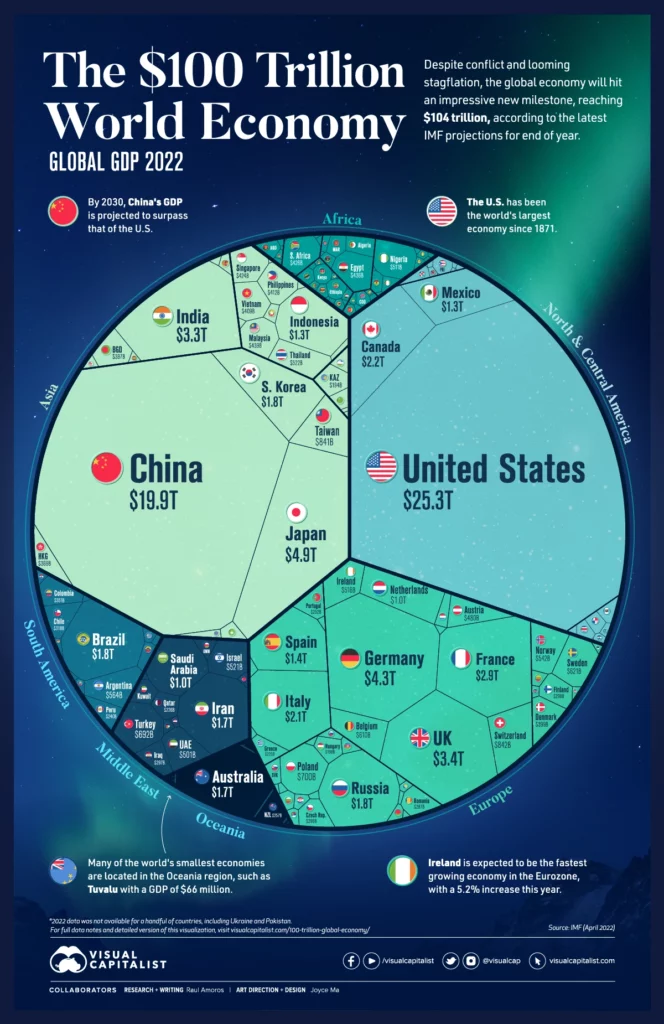
Food For Thought
You’ll probably have to go to the site to really zoom in and see the information in this stunning graphic, but it is definitely worth it.
Featured Image: Photo by Dario Morandotti on Unsplash




 January News from Information Security
January News from Information Security

