Welcome to the much-delayed December newsletter. I realize this newsletter finds most of you in the throes of the end of the semester, whether that is taking final exams, administering final exams, dealing with grades, stressed students, or stressed professors, or just realizing that December has arrived and the semester and everything about it wraps up in days. Then you all get to consider more personal tasks and endeavors. It doesn’t slow down any time soon. I’m sorry. But, here is the December newsletter. Please take a few minutes to read through it. I have only two topics and neither of them will take a great amount of time to look over.
First, I would like to thank everyone for their efforts to complete the fall cybersecurity awareness training. We’ve had fantastic participation and I’m encouraged that so many of you took the time to complete it. With that said, I want to relate a story that some of you may have already heard about. It relates directly to WHY we do cybersecurity awareness training.
Guilford College in North Carolina is a small liberal arts college, smaller than Berry. It was hit with ransomware and some sensitive faculty, staff, and student data was stolen. This happened in October. You can read a fairly brief synopsis here at The Record. The root cause of the hack is not revealed in the article, but my information security Spidey-sense suggests that it probably started with a phishing email. It most likely blossomed from there, allowing the attackers into the Guilford system. Once in, they continued to gain more privileges and access, ultimately resulting in an installation of ransomware and the theft of data. This may be completely wrong, but over 70% of successful attacks start with a phishing email.
This is why we conducted training this fall and why we will continue to conduct training every fall and spring semester, along with simulated phishing attacks like the ones we did in October. While I was pleased with the low number of people who fell for these emails, it only takes one to start a successful attack, so we will continue to conduct simulated phishing attacks. Please be skeptical with any email that seems even a little suspect. Report it and I will be glad to evaluate it. I would rather evaluate a hundred false positive reports a day than have someone fall for a real phishing attempt. There’s a Quick Info on how to report phishing emails on the Cybersecurity News & Alerts site. Take a look and be sure to report any suspicious emails.
Next, I’d like to inform you all about an improvement to an existing tool you can use to help protect your account. Everyone has multi-factor authentication (MFA) enabled on their account. The Microsoft Authenticator makes it easy to do MFA, with its simple Approve or Deny buttons. Sometimes, you might get a MFA request when you didn’t expect one. They can happen at any time, day or night. Right now, the Authenticator doesn’t provide any information about why it is requesting you to Approve or Deny a login.
Starting in December, the app will provide two crucial pieces of information to help you decide whether to Approve or Deny the request. The first piece of information will be the name of the application making the request. If you are signing into the MyApps portal, it will say “My Apps”. If you are logging in to the Outlook Web Access page mail.berry.edu, it will say “Office 365 Exchange Online”.
The second piece of information the app will provide is the location of the device attempting to log in to your account. If you are on campus, the location should say “GA, United States” and show Rome on the map, as shown below:
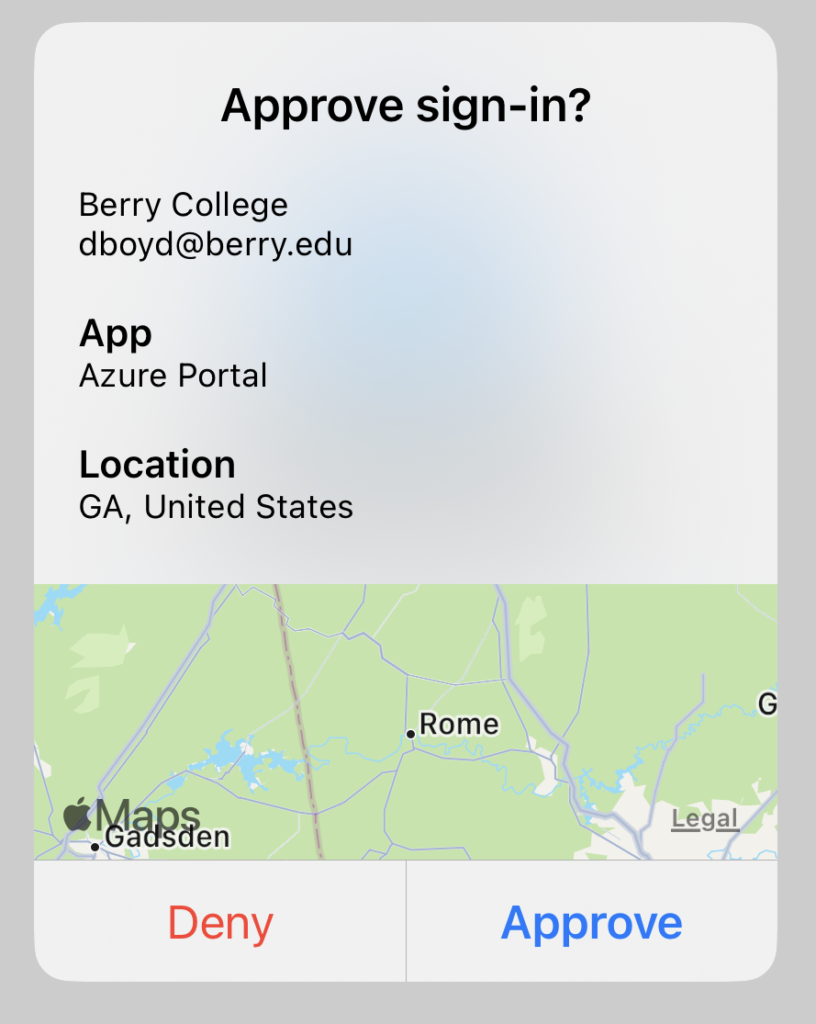
If you are at home during break and attempt to log in to see your email or grades, it should show your location, where ever that is. If you get an unexpected MFA request that shows something else, say like Russia, or Vietnam, or some other foreign country, or even another state, you should be VERY suspicious and probably deny the request.
With these two crucial pieces of information, we hope everyone is able to be confident about approving or denying any request that comes to their app. We hope to have this enabled shortly after the semester ends; at the latest, before you return for spring semester. If you are not using the app at this time, we strongly encourage you to do so. This is the most secure way to use MFA within our system. Phone calls and texts are NOT secure and will most likely be phased out of use in the future.
I almost forgot…we mentioned in the last newsletter how we were going to encourage everyone to report phishing emails by incentivizing the activity. We will begin to do this in January, so remember to report those phishing emails! Everyone who reports a phishing email in January will be included in a drawing for a “groovy” desktop fidget toy.
That’s it for this newsletter. I hope everyone has a safe and stress-free holiday break and we look forward to seeing you back in January, unless you are graduating; in that case, good luck with your next step in life.
All Berry students, faculty and staff have MFA enabled on their Berry account, and you should use it in the most secure way via the Microsoft Authenticator app on your smart phone. But don’t stop there! Use the Microsoft Authenticator as your second factor on any site that supports Google Authenticator. Turn MFA/2FA on everywhere you can. Yes, it will take you another few seconds to log in, but your data and account will be safer.
If I’m not covering a topic of cybersecurity you are interested in or concerned about, please let me know. I want to be your first and best resource on cybersecurity information, so let me know how I can help and inform you.
If you’re not following Berry OIT on Facebook (@BerryCollegeOIT), Twitter (@berryoit), or Instagram (@berrycollegeoit), you should be, as more information from OIT and specifically Information Security, will be provided using these outlets. If you are not into social media, you can also subscribe to get updates via email. Just use the link available in the right-hand sidebar on the current posts page.
You can always check back here for warnings about current phishing emails, confirmations of valid emails you might have a question about, and data breach notifications. There’s also the events calendar where events will be posted, like Cybersecurity Awareness Month.
Food For Thought
This month’s food for thought comes from none other than one of my favorite YouTubers, CGP Grey. Have you ever wondered about those letters on your airline tickets and baggage claim tags? Some of them make sense, like ATL for Atlanta’s Hartsfield-Jackson Airport, but others are less certain, like BNA for Nashville International Airport (which used to be called Berry Field, hence the B), or just ridiculous like Kansas City International Airport which is…MCI, which also has a history behind it. But just watch the video…it will (attempt) to explain it all.
Featured Image: Image by Brant Sanderlin/Berry College

 December News from Information Security
December News from Information Security



