Welcome to 2023 and welcome back to Berry! I want to congratulate you for surviving the holidays and deciding to come back to campus for a brand new year and brand new semester. There are LOTS of things to discuss this month, including Data Privacy Week, a reminder about updates to our login security, and some tips for you LastPass, Tiktok, and Twitter users.
First up is Data Privacy Week. The National Cybersecurity Alliance, the same organization that “sponsors” Cybersecurity Awareness Month in October also promotes Data Privacy Week (DPW), which used to be Data Privacy Day. The threats to privacy have become quite overwhelming, so the campaign was expanded from a day to a week. This year DPW is January 22-28.
Everything we do online creates data for someone. What data, how it is used, and what we can do to control it are the focus of DPW. The goal is help everyone think about what information they share with apps and websites, then help them understand the implications of sharing that data. A 2022 consumer privacy survey by Cisco revealed the following:
- 89% of people say they care about data privacy
- 43% said they are unable to protect their data effectively.
- 79% say that it’s too hard for them to know and understand how companies are using their data.
Those numbers are not shocking, but they are sobering. Do you know how to protect your data through privacy controls and settings in apps and on websites? If not, or if you think you might need a refresher, go to this page provided by the National Cybersecurity Alliance. The page provides some basic tips, but has a link to another page that shows specific steps for dozens of websites and apps. If you are looking for a specific app or website, you can jump directly to this page by clicking here.
Be on the lookout for posters around campus with more tips and ideas during that week.
This was mentioned in the December newsletter, but we’ve all slept and celebrated since then, so I am posting it again in this newsletter. We are changing the look and usefulness of the Microsoft Authenticator. Everyone has multi-factor authentication (MFA) enabled on their account. The Microsoft Authenticator makes it easy to do MFA, with its simple Approve or Deny buttons. Sometimes, you might get a MFA request when you didn’t expect one. They can happen at any time, day or night. Right now, the Authenticator doesn’t provide any information about why it is requesting you to Approve or Deny a login.
Now the app will provide two crucial pieces of information to help you decide whether to Approve or Deny the request. The first piece of information will be the name of the application making the request. If you are signing into the MyApps portal, it will say “My Apps”. If you are logging in to the Outlook Web Access page mail.berry.edu, it will say “Office 365 Exchange Online”.
The second piece of information the app will provide is the location of the device attempting to login to your account. If you are on campus, the location should say “GA, United States” and show Rome on the map, as shown below:
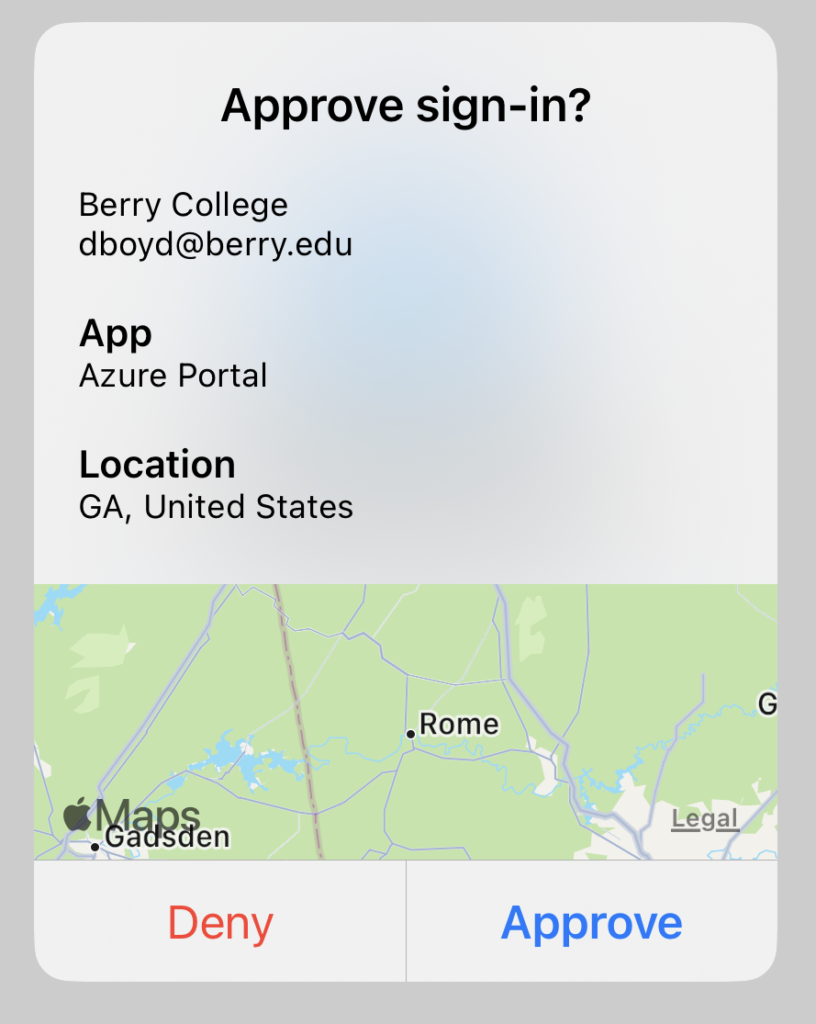
If you are at home during a break and attempt to log in to see your email or grades, it should show your location, wherever that is. If you get an unexpected MFA request that shows something else, say like Russia, or Vietnam, or some other foreign country, or even another state, you should be VERY suspicious and probably deny the request.
With these two crucial pieces of information, we hope everyone is able to be confident about approving or denying any request that comes to their app. If you are not using the app at this time, we strongly encourage you to do so. This is the most secure way to use MFA within our system. Phone calls and texts are NOT secure and will most likely be phased out of use in the future.
Yes, LastPass experienced an incident that compromised user data. If you want the gory details, check out this Bleeping Computer article that does a great job of explaining what happened. The TL;DR version goes like this – hackers got hold of copies of customer password vaults, which means they can attempt to “break these vaults open” at their leisure. Some of the data in these vaults is NOT encrypted, including website addresses. This is not a concern unless you put information in the unencrypted fields that you intended to be kept private.
The big question is “if I am a LastPass user, should I worry?”. The answer, of course, is “maybe”. IF you followed LastPass’s recommendations for your master password, then you are probably OK for a few years. If you used “password”, “123456” (probably not allowed by LastPass, but I’m trying to make a point here), or something similarly ridiculous, then YES, you should worry. Once they crack your master password, they then have access to ALL of your passwords stored in the vault.
If you know you used a weak master password, or even just suspect it, this is my “simple, not easy”, suggested plan of action:
- Change your master password to one that meets or preferably exceeds the LastPass recommendations. This means your master password is 12 or more characters long (20 is better), uses upper case and lower case letters, numbers and special characters
- Go through your entire vault and change the password for every account you have in it. You’ll probably find some entries you no longer need or use…in that case, don’t just delete them from the vault, be sure the account doesn’t exist anymore.
It is unfortunate that LastPass lost customer data, but it is not the end of the world. There’s nothing the hackers can really do except try to brute-force crack some user vaults.
Now, as far as TikTok, I can only say that you should use this app/service with caution. There are major privacy concerns related to TikTok and the federal government has banned the use of the app on government equipment and networks. The big question here is “will Berry ban it from its network?”. I honestly don’t have an answer at this time, but I do want to make one very important point – You should not use TikTok on any device that also has access to Berry College data. I’m not really talking about individual information, I’m more concerned with college data files that are incidentally available on a phone. Data stored in Microsoft Teams and OneDrive can be accessed on phones that also may be running TikTok. Please be very careful if you do this and be on the lookout for more information from this office about the developing story of TikTok.
The last application/website in our hall of shame this month is Twitter, who admitted that data had been “scraped” from Twitter associating email addresses with Twitter handles way back in 2019. Now that data, consisting of over 200 million accounts and nearly 400 Berry accounts, has been traded on dark web sites. There are no passwords involved, just a lot of data that could be used to convincingly phish you. Be very careful with any communication from Twitter, particularly in the next few weeks as cyber-criminals attempt to leverage this trove of data.
Whew! That was a lot! Don’t forget, we are encouraging everyone to report phishing emails by incentivizing the activity. We will start this now, in January, so remember to report those phishing emails! Everyone who reports a phishing email in January will be included in a drawing for a “groovy” desktop fidget toy. Don’t know how to report a phishing email? Check out the Quick Info page located on this very site.
As mentioned already in this newsletter, all Berry students, faculty and staff have MFA enabled on their Berry account, and you should use it in the most secure way via the Microsoft Authenticator app on your smart phone. But don’t stop there! Use the Microsoft Authenticator as your second factor on any site that supports Google Authenticator. Turn MFA/2FA on everywhere you can. Yes, it will take you another few seconds to log in, but your data and account will be safer.
If I’m not covering a topic of cybersecurity you are interested in or concerned about, please let me know. I want to be your first and best resource on cybersecurity information, so let me know how I can help and inform you.
If you’re not following Berry OIT on Facebook (@BerryCollegeOIT), Twitter (@berryoit), or Instagram (@berrycollegeoit), you should be, as more information from OIT and specifically Information Security, will be provided using these outlets. If you are not into social media, you can also subscribe to get updates via email. Just use the link available in the right-hand sidebar on the current posts page.
You can always check back here for warnings about current phishing emails, confirmations of valid emails you might have a question about, and data breach notifications. There’s also the events calendar where events will be posted, like Cybersecurity Awareness Month.
Food For Thought
With the release of ChatGPT (what’s that you say? check here for more info), I wanted to present a sobering video about the rise of automation by one of my favorite YouTubers that I’ve featured here before – CGPGrey. This fifteen minute video might be a bit depressing for those of us in higher education, but it is DEFINITELY food for thought.

 January (2023) News from Information Security
January (2023) News from Information Security


 Welcome to Data Privacy Week 2022!
Welcome to Data Privacy Week 2022!
